Algorithm And Logarithm Differences
Analyze the efficiency of algorithms. The mean is the same as the average.

What Is The Difference Between A Logarithm And An Algorithm Quora
Schoeberls Netgen algorithm 12.
Algorithm and logarithm differences. This means if we fold a piece of paper in half six times it will have 64 layers. Creation of digital signatures. It is based on mathematical concept of modular exponentiation and discrete logarithm.
Note that difference values assume that the counter can wrap. Digital Signature Algorithm DSA. Evolutionary algorithms EAs as meta-heuristic techniques have been shown to be effective solvers for many real-world problems over the past few decades Apart from their strong capability of tackling non-convex and multi-model problems EAs do not reply on analytic and differential objective functions and are able to perform optimization on.
110 Yi-Kai Liu Quantum algorithms using the curvelet transform. In mathematics the logarithm is the inverse function to exponentiationThat means the logarithm of a given number x is the exponent to which another fixed number the base b must be raised to produce that number xIn the simplest case the logarithm counts the number of occurrences of the same factor in repeated multiplication. Well be looking at time as a resource.
Since 1000 10 10 10 10 3 the logarithm. We say f is Ogn read. Following our popular article explaining what Adobe did wrong with its users passwords a number of readers asked us Why not publish.
Digital signature algorithm DSA Elliptic curve cryptography ECC RSA vs DSA vs ECC Algorithms. Note also that 2 On and O2 n are not the same. Because these ratios can encode some form of meaning this information gets encoded as vector differences as well.
The RSA algorithm was developed in 1977 by Ron Rivest Adi Shamir and Leonard Adleman. Comparing Orders of Growth. The term Λβ ie the logarithm of the density of the normal prior up to an additive constant can be read as a ridge penalty term and therefore we perform the optimization using the iteratively reweighted ridge regression algorithm also known as weighted updates.
Subtraction is an arithmetic operation that represents the operation of removing objects from a collection. Namely log p natural logarithm we have an objective that has a larger dynamic range than raw. Logarithm is the opposite of exponentiation.
Proceedings of STOC 2009 pg. What is the difference between RSA and DSA. It uses asymmetric key encryption for communicating between two parties and encrypting the message.
A procedure or set. There is no known solution to the mathematical problem posed by the equation that produces the elliptical curve in a graph and so the only solution is to try random numbers. ElGamal encryption is a public-key cryptosystem.
Then a three-dimensional version of the 2D Delaunay algorithm described above is applied to insert points in the volume to respect the mesh size constraints. It involves four operations. So the difference between an IP ID of 65100 followed by a value of 700 is 1136.
Syncmers are better than minimizers Video talks on 16S data analysis posted. Know the differences between O1 On Olog n and On2. Secure Hash Algorithm SHA.
Here log means log 2 or the logarithm base 2 although the logarithm base doesnt really matter since logarithms with different bases differ by a constant factor. Idea of ElGamal cryptosystem. That is 5 2 3.
Owing to the fact that the logarithm of a ratio equals the difference of logarithms this objective associates the logarithm of ratios of co-occurrence probabilities with vector differences in the word vector space. It is used for digital signature and its verification. The study of the performance of algorithms or algorithmic complexity falls into the field of algorithm analysis.
Log2 x Return the base-2 logarithm of x. The difference between 2000 followed by 1100 is. 20 of taxonomy annotations in SILVA and Greengenes are wrong Taxonomy prediction is.
Both algorithms use modular arithmetic but the RSA certificate relies on prime factorization while DSA uses the discrete logarithm problem. Quantum Information and Computation Vol. Both return values have the same sign.
Asymmetric-key algorithms are mostly based on mathematical problems like integer factorization and discrete logarithm problem. DSA stand for Digital Signature Algorithm. Log10 x Return the base-10 logarithm of x.
Visualize runtime differences with experiments. Main uses of asymmetric algorithms are. First its the algorithms use of mathematical problems.
This cryptosystem is based on the difficulty of finding discrete logarithm in a cyclic group that is even if we know g a and g k it is extremely difficult to compute g ak. SHA-1 was deprecated by NIST as of the end of 2013. For each of these tests the targets IP ID generation algorithm is classified based on the algorithm below.
It will help us recognize the differences between RSA and DSA encryption. The algorithm then repeats this process of evaluating the gradient and taking steps until it considers that it is eventually reached the maximum expected return. F is order g if g is an upper bound on f.
Add up a series of numbers and divide the sum by the total. 120000 new RNA virus species discovered by mining the SRA. Typically the less time an algorithm takes to complete the better.
Log x Return the natural logarithm of x. Return the natural logarithm of the gamma function of x. 111 Wim van Dam and Igor Shparlinski.
Since 2 x 2 x 2 x 2 x 2 x 2 64 2 6 64. The ECC algorithm works on Elliptic Curve Discrete Logarithm Problem ECDLP that is hard to crack for hackers. 2 x 64.
Algorithm analysis answers the question of how many resources such as disk space or time an algorithm consumes. A graphical representation of data that shows differences in distributions and plots data set ranges. O Let f and g be functions from positive integers to positive integers.
Differences between Hash functions Symmetric and Asymmetric algorithms. Shors discrete logarithm quantum algorithm for elliptic curves. Where the differences are that gradient descent is designed to find the.
It was developed by National Institute of Standards and Technology NIST in 1991. Specifically the updates for a given gene are of the form. Subtraction is signified by the minus sign For example in the adjacent picture there are 5 2 peachesmeaning 5 peaches with 2 taken away resulting in a total of 3 peaches.
Analyze a few classic algorithms Linear Search Binary Search Selection Sort. The HXT algorithm 13 is a new efficient and parallel reimplementaton of the Delaunay algorithm. The Frontal algorithm uses J.
Minor differences between tests are noted. URMAP ultra-fast read mapper paper. Algorithm for NISTs Secure Hash Standard SHS described in FIPS PUB 180-4 The status of NIST hash algorithms can be found on their Policy on Hash Functions page.
You are given a string s of length nThe prefix function for this string is defined as an array pi of length n where pii is the length of the longest proper prefix of the substring s0 dots i which is also a suffix of this substring. KnuthMorrisPratt algorithm Prefix function definition. Modf x Return a tuple of two floats being the fractional and integral parts of x.
If nx a the logarithm of a with n as the base is x. Therefore the difference of 5 and 2 is 3. SHA-1 produces a 160-bit hash value and was originally published as FIPS PUB 180-1 and RFC 3174.
It relies on the fact that factorization of large prime numbers requires significant computing power and was the first algorithm to take advantage of the. To establishdistribute session keys such as in case of TLS protocol. A proper prefix of a string is a prefix that is not.

What Does O Log N Mean Exactly Stack Overflow
Difference Between Flowchart And Algorithm Comparison Chart
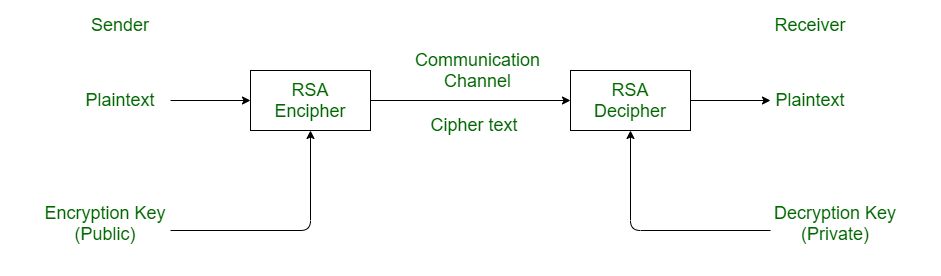
Difference Between Rsa Algorithm And Dsa Geeksforgeeks

Algorithms And Logarithms A User S Guide Hubpages
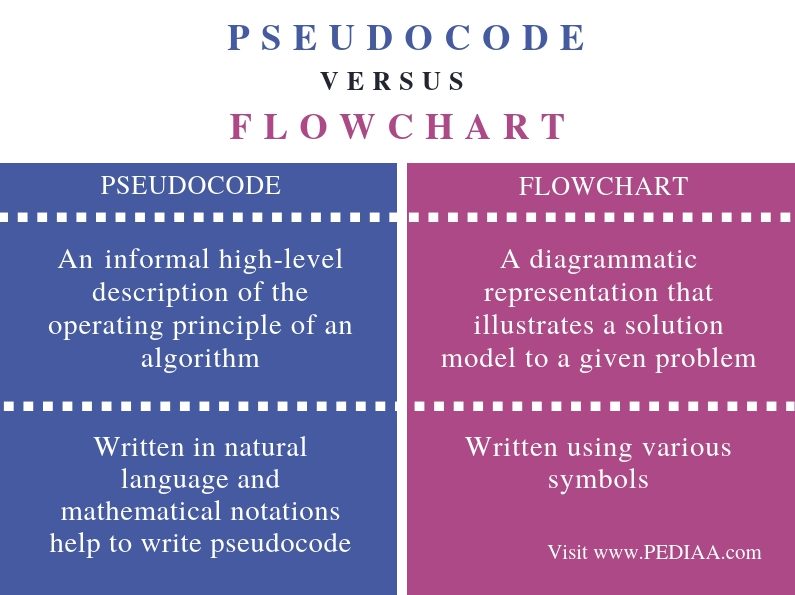
What Is The Difference Between Pseudocode And Flowchart Pediaa Com

Difference Between Ln And Log Youtube
How Can We Calculate The Logarithms By Hand Without Using Any Calculator Quora
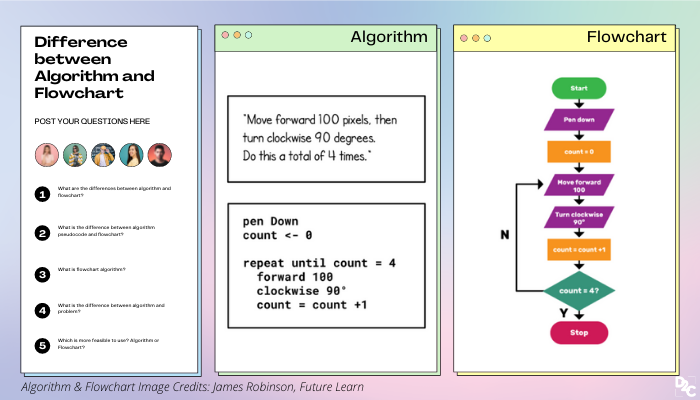
Difference Between Algorithm And Flowchart Explained D2c
Is O Log N Always Faster Than O N 2 Quora

Time Complexity Analysis In Data Structure And Algorithms
How Can We Calculate The Logarithms By Hand Without Using Any Calculator Quora

Big O Logarithmic Time Complexity Jarednielsen Com

What Does O Log N Mean Exactly Stack Overflow

An Em Algorithm For The Estimation Of Gmcm Parameters Step 1 Computes Download Scientific Diagram
Math Fun Library Algorithm And Logarithm

Algorithms And Logarithms A User S Guide Hubpages

Time Complexity Of Algorithms Open4tech

Komentar
Posting Komentar