Cryptographic Algorithms List

Signature And Encryption Options For Oauth 2 0 And Oidc Part 2 Forgerock Developer
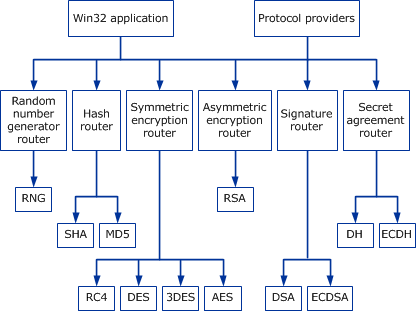
Cryptographic Primitives Win32 Apps Microsoft Docs

Blog Which Algorithms Are Fips 140 3 Approved

Overview Of The Cryptographic Encryption Algorithms Download Scientific Diagram

Isara Radiate Quantum Safe Toolkit Isara Corporation

Different Symmetric Asymmetric Cryptographic Algorithms Download Scientific Diagram

Different Encryption Algorithms In Java Toolbox It Security

List Of Supported Encryption Algorithms And Its Main Features Download Table

System Security Cryptography Namespace In Net

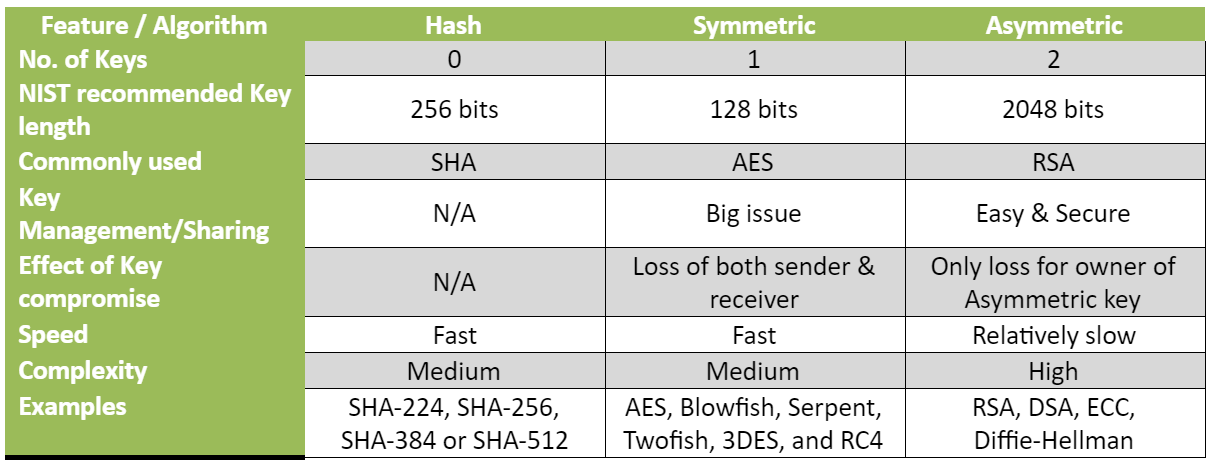
Differences Between Hash Functions Symmetric Asymmetric Algorithms

Hashing Vs Encryption What S The Difference Cybernews

Pdf Critical Analysis Of Some Cryptography Algorithms Semantic Scholar

List Of Recent Lightweight Cryptographic Algorithms Download Table

Pdf Critical Analysis Of Some Cryptography Algorithms Semantic Scholar

A Comparison Of Cryptographic Algorithms Des 3des Aes Rsa And Blowfish For Guessing Attacks Prevention
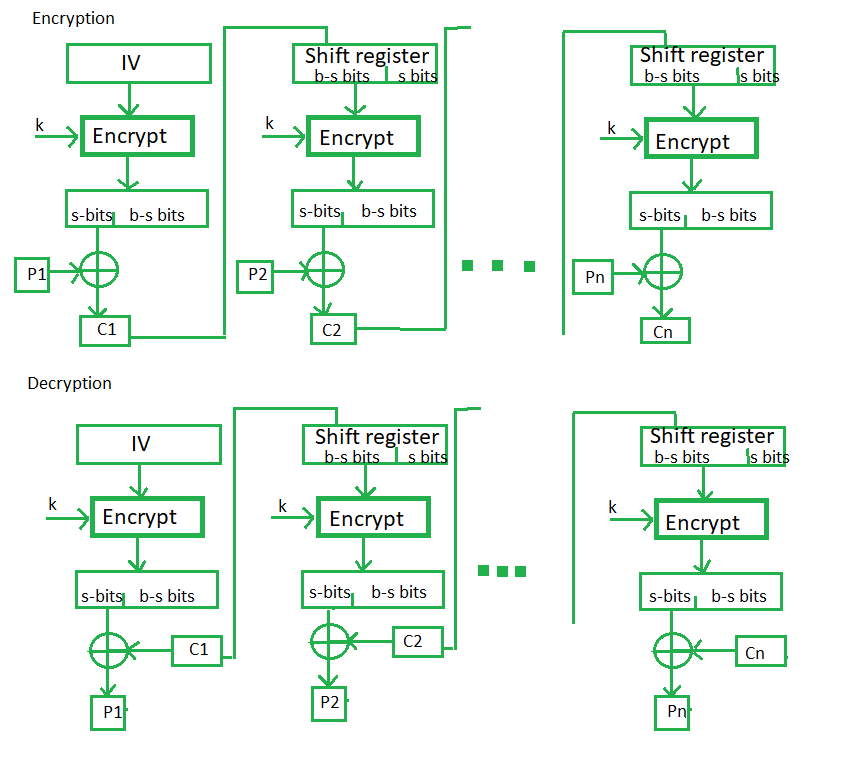
Block Cipher Modes Of Operation Geeksforgeeks

List Of Recent Lightweight Cryptographic Algorithms Download Table

List Of Supported Encryption Algorithms And Its Main Features Download Table

Blog Which Algorithms Are Fips 140 3 Approved
Komentar
Posting Komentar